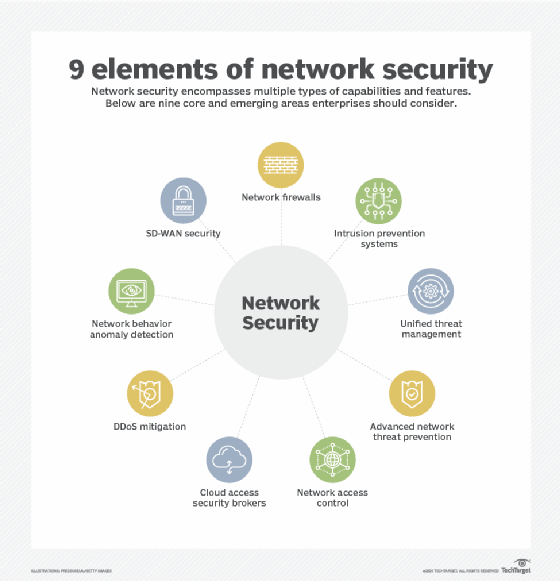
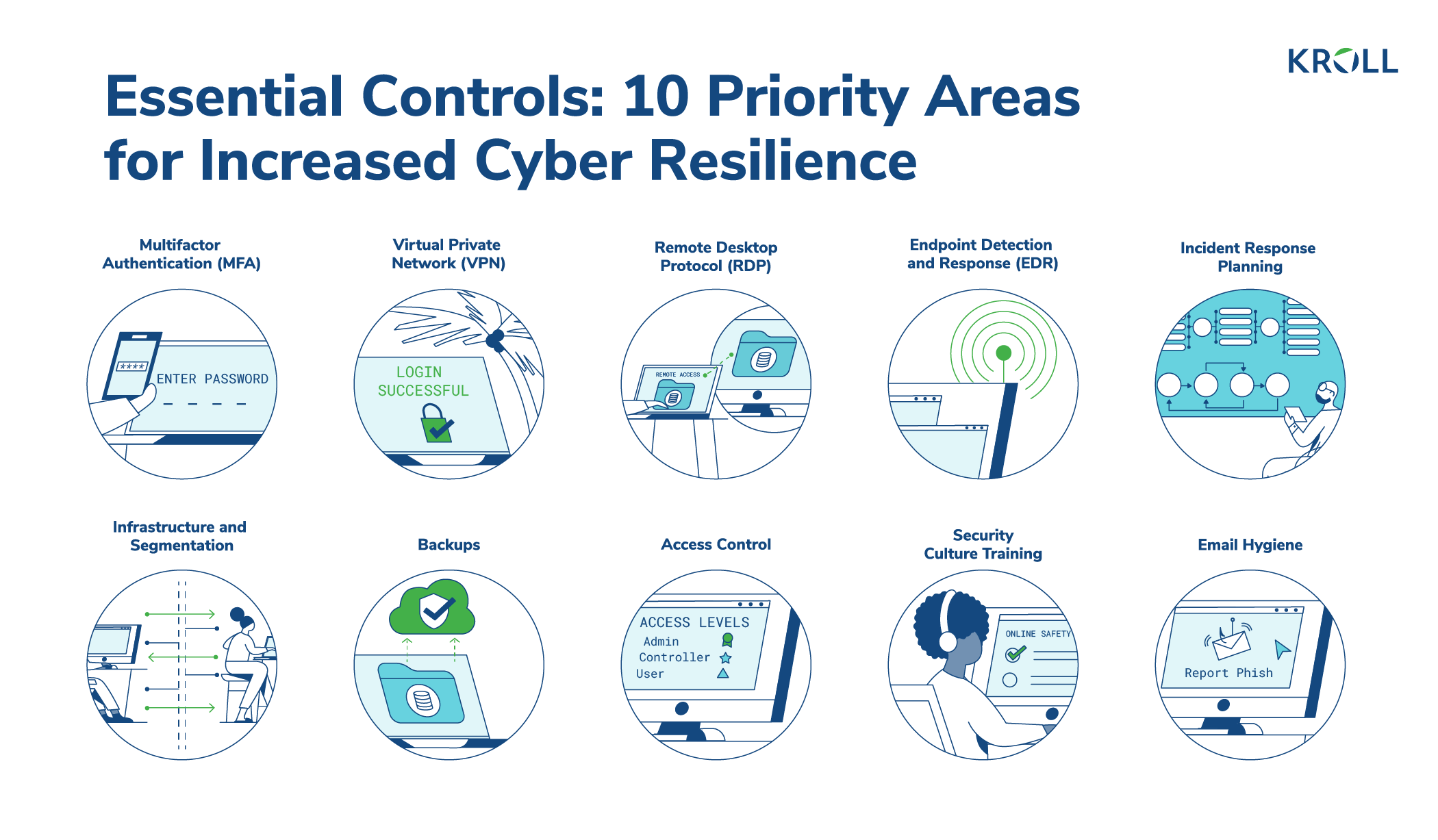
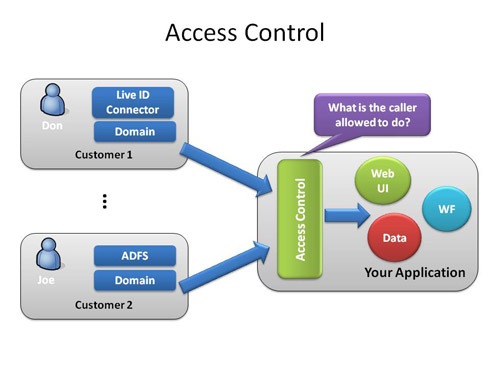
A Guide to Claims-Based Identity and Access Control: Authentication and Authorization for Services and the Web: Authentication and Authorization for Services, Web, and the Cloud : Baier, Dominick, Bertocci, Vittorio, Brown, Keith,
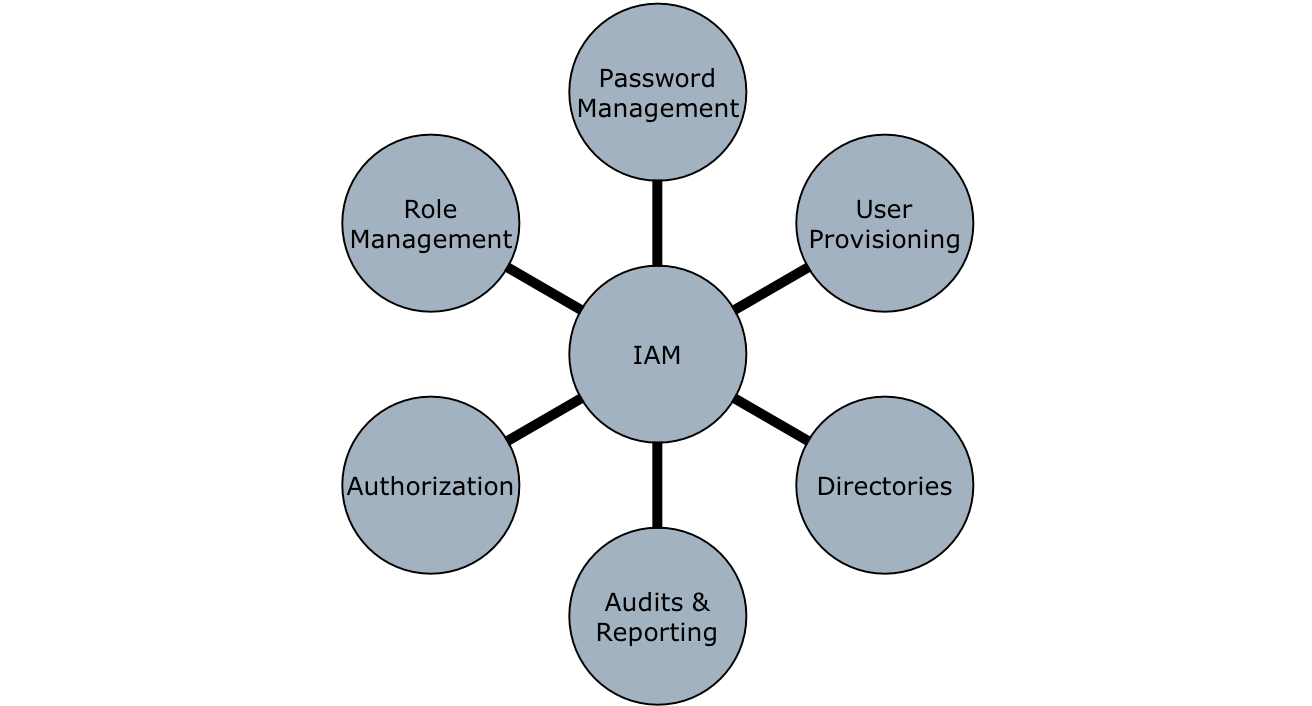
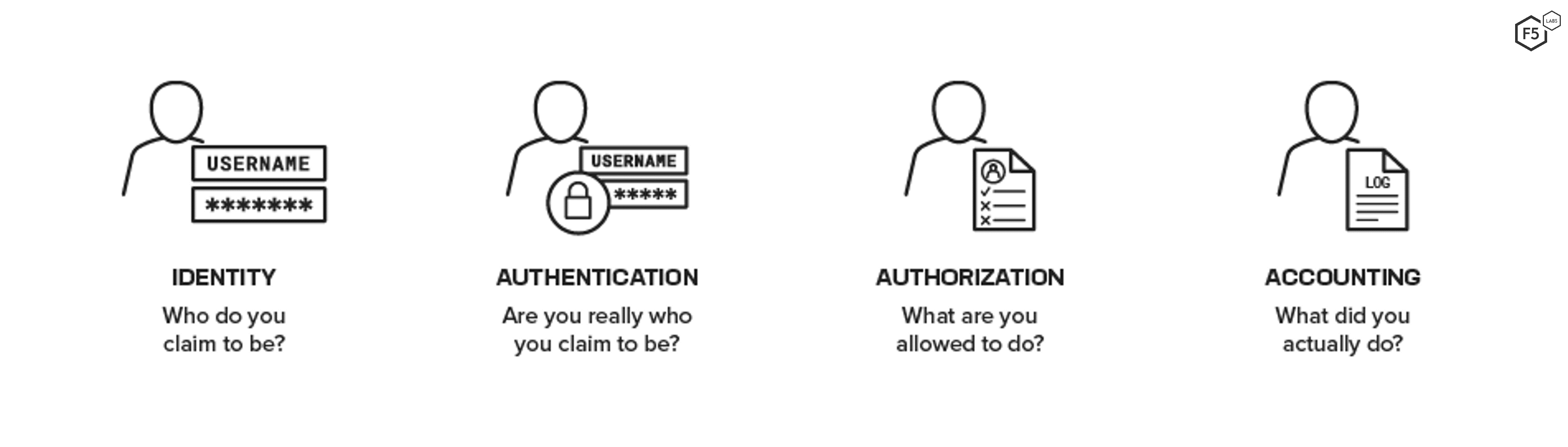
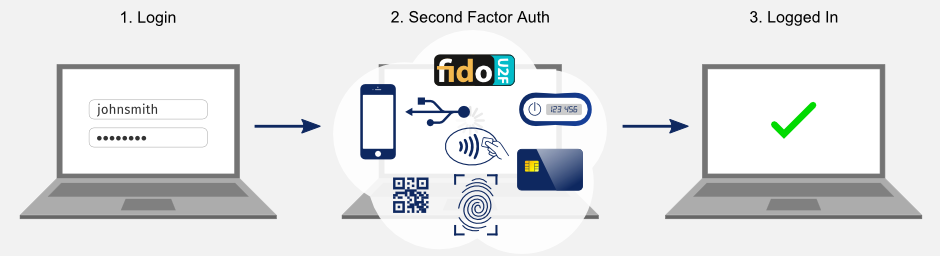
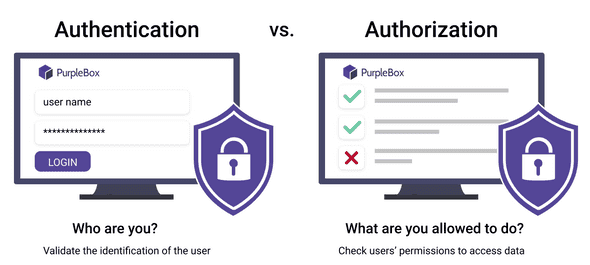
3 Basic A's of Identity and Access Management -Authentication, Authorization, and Accounting – Xorlogics